What Is Tor and Its Key Features
Before diving into how Tor works, it’s important to understand what it actually is and why it stands out among privacy tools. Tor isn’t just another browser—it’s a unique system built to safeguard your identity online. Let’s break down the basics and explore its most important features.
Getting to Know Tor
Tor is a free, open-source software project designed to protect user privacy and anonymity online. It routes your internet traffic through a decentralized network of volunteer-operated servers, also known as nodes or relays.
Instead of connecting directly to a website, your traffic passes through multiple relays, making it much harder for anyone to trace your activity back to you.
🔑 In simple terms: Tor hides your IP address by bouncing your traffic around the world.
Core Features of Tor Browser
The Tor Browser, built on Firefox, is the most popular way to use the Tor network. Key features include:
- Multi-layer encryption: Traffic is encrypted multiple times, like layers of an onion.
- Traffic anonymization: Your browsing activity is routed through at least 3 nodes.
- No tracking: Advertisers and websites have a harder time fingerprinting you.
- Free to use: Tor is community-driven and open-source.
What Are Onion Services?
Onion services (formerly called hidden services) are websites hosted within the Tor network. They use the “.onion” domain and can only be accessed via Tor.
Examples of onion services:
- Secure communication tools (like ProtonMail’s.onion site)
- Whistleblower platforms
- Dark web marketplaces (many are illegal)
💡 Note: Not all onion services are harmful. Some are used by journalists, activists, and organizations for censorship resistance and privacy protection.
Where Can You Use Tor Browser?
Tor Browser can be used anywhere in the world, but its value is most evident in countries or regions where online freedom and privacy are limited. Here are some common scenarios:
- Private Browsing Worldwide
Many users rely on Tor to prevent advertisers, internet providers, or data brokers from tracking their online activity. - Bypassing Internet Censorship
In countries like China, Iran, or Russia, certain websites and apps are blocked. Tor allows users to bypass these restrictions and access information freely. - Supporting Free Speech
In regions with strict government surveillance, such as parts of the Middle East or Southeast Asia, journalists and activists use Tor to communicate securely and protect their identities. - Dark Web Access
Tor is the only way to safely reach onion websites on the dark web. However, this should be done with caution since not all content is safe or legal. - Additional Security in Democratic Countries
Even in places like the United States or European Union, where the internet is more open, Tor is used by individuals who want extra layers of privacy—for example, researchers, lawyers, or anyone handling sensitive data.
👉 Whether you’re avoiding trackers in a free country or fighting censorship in a restrictive one, Tor provides a universal solution for protecting anonymity.
Is Using Tor Legal?
In most countries, using the Tor Browser is completely legal. The technology itself—built to enhance privacy and protect anonymity—is not illegal. What really matters is how you use it. For example:
Legal use cases: browsing news sites, protecting personal privacy, or communicating securely.
Illegal use cases: purchasing drugs, weapons, or stolen data on the dark web.
That’s the distinction: Tor is legal, but certain activities conducted through it may not be.
Some governments, such as those in China, Iran, and Russia, actively attempt to restrict or block Tor connections. Yet, many users in those regions still manage to access the network using Tor bridges, which are special entry points designed to bypass censorship.
From a VPN and privacy technology perspective, it’s important to highlight that while Tor provides anonymity, pairing it with tools like a VPN(like UFO VPN) can offer additional protection. For users in restrictive countries, this combination can make access more reliable while still keeping traffic secure.
📌 Key takeaway: Tor is generally legal, but the legality of your activities depends on local laws. Always use Tor responsibly and understand the regulations in your country before relying on it.
🌍 Tor Legal Status by Country
- United States: Tor is fully legal to use. However, engaging in illegal activities through Tor remains punishable by law.
- European Union: Tor is legal across most EU countries. It is widely used by privacy advocates and journalists.
- China: Tor is restricted and officially blocked. Some users bypass these restrictions using Tor bridges or VPNs.
- Russia: Restricted, with government censorship targeting Tor nodes. Access is limited and unstable.
- Iran: Heavily censored. Direct Tor connections are blocked, but some users rely on obfuscation tools to access the network.
- United Arab Emirates: Limited use allowed. Tor itself is not banned, but activity is closely monitored, and misuse may lead to legal issues.
- India: Tor is legal to use. However, activities on the darknet or illegal use remain prohibited.
Tor is legal in most open and democratic countries (like the US, EU, and India). However, in regions with strict censorship (such as China, Russia, and Iran), Tor is restricted, blocked, or heavily monitored. Always review your local laws and regulations before using Tor to avoid legal risks.
Tor Browser vs. VPN: What's the Difference?
Both Tor and VPNs protect privacy, but they work differently.
| Feature | Tor Browser | VPN |
|---|---|---|
| Encryption | Multi-layer (“onion” routing) | End-to-end encryption |
| Speed | Slow (multiple relays) | Fast (single server route) |
| Anonymity | Strong anonymity, hard to trace | Strong privacy, but VPN sees your IP |
| Access | Dark web & onion services | Regular web, geo-unblocking |
| Best For | High anonymity, whistleblowing, research | Streaming, security, daily browsing |
💡 Many users combine both: VPN + Tor. This hides your Tor usage from your ISP and adds another layer of protection.
How to Use Tor Safely
Using the Tor Browser adds an important layer of privacy, but it doesn’t make you invincible online. To truly stay safe, you need to combine Tor with smart security habits. Here are the best practices:
- Download from Official Sources
Always get Tor Browser from the official Tor Project website
Avoid third-party “Tor downloads,” as they may contain malware or backdoors. - Keep the Browser Updated
Updates fix vulnerabilities that attackers could exploit.
Enable automatic updates so you don’t miss critical security patches. - Limit Personal Logins
Avoid logging into accounts that reveal your real identity (e.g., Gmail, Facebook, online banking).
If you must log in, use separate accounts created specifically for Tor. - Prevent Browser Fingerprinting
Do not resize or maximize your Tor Browser window—doing so makes you more identifiable.
Stick to the default security settings unless you’re sure about the risks. - Be Careful with Downloads
Files (especially PDFs, Word docs, and executables) may contain hidden tracking code.
If you must download, open files only on a secure, offline, or virtual machine environment. - Combine Tor with a VPN for Extra Protection
A VPN hides your Tor usage from your ISP and prevents potential Tor entry node surveillance.
For example, connecting to a VPN first and then opening Tor (known as “Tor over VPN”) ensures your IP address remains hidden from both your ISP and Tor’s entry relay.
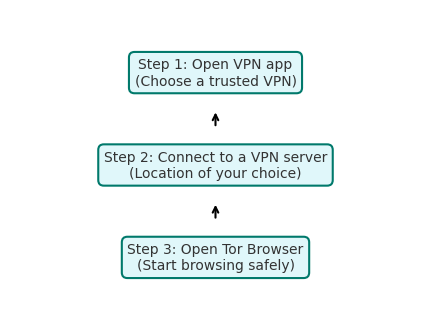
📌 Key Takeaway: Tor enhances anonymity, but its effectiveness depends on your behavior. Pairing Tor with safe browsing habits—and optionally a VPN—gives you the best balance between privacy and security.


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







Risks & Limitations of the Tor Network
While Tor is a powerful tool for anonymity, it is not flawless. To use it wisely, it’s important to understand its risks and limitations.
Potential De-anonymization Threats
- Compromised Tor nodes: Law enforcement agencies or attackers may run Tor relays to observe traffic patterns. While Tor encrypts traffic within the network, entry and exit nodes can still provide clues about users.
- Personal logins reveal identity: If you log into accounts tied to your real identity (e.g., Gmail, Facebook, online banking), your anonymity is broken regardless of Tor’s protection.
- Traffic correlation attacks: Skilled attackers may match your incoming and outgoing traffic to deanonymize you.
Sybil & Routing Attacks
- Sybil attacks: An adversary may operate many fake relays in the Tor network. If your traffic flows mostly through these malicious relays, they can monitor or manipulate it.
- Routing attacks: Exit nodes (the final server before your traffic reaches its destination) can tamper with unencrypted traffic. This is especially risky when visiting HTTP (non-HTTPS) websites.
📌 Tip: Always check for HTTPS when browsing with Tor.
Performance & Accessibility
- Slower browsing speed: Tor routes traffic through multiple relays worldwide, which increases latency compared to direct connections.
- Blocked access: Some websites and online services block Tor traffic entirely, making them inaccessible without extra tools such as Tor bridges or a VPN.
- Unstable connections: Because the Tor network is volunteer-based, performance can vary depending on the quality and availability of relays.
Malware & Dark Web Risks
- No malware protection: Tor does not filter out malicious software. Downloading unknown files or visiting unsafe sites can still infect your device.
- Dark web dangers: While the dark web hosts legitimate sites, it’s also home to scams, phishing pages, and illegal marketplaces. Users who explore it without caution can fall victim to fraud or legal consequences.
📌 Important reminder: Tor enhances anonymity but does not guarantee safety against malware, phishing, or law enforcement monitoring. Treat it as one layer of protection—not a complete cybersecurity solution.
Conclusion
Tor is a powerful ally for online anonymity, but it’s not flawless. Its slower performance, risks of malicious exit nodes, and potential exposure on the dark web mean you should use it with caution.
✅ To stay safe with Tor:
Download only from the official Tor Project website.
Avoid logging into personal accounts or engaging with suspicious sites.
Combine Tor with a trusted VPN to hide your Tor usage from your ISP and add an extra layer of encryption.
👉 By pairing Tor with a reliable UFO VPN, you get the best of both worlds: strong anonymity with Tor and fast, secure, everyday protection with a VPN. This way, your privacy isn’t just anonymous—it’s also safeguarded.
FAQs
Q1:Can I use Tor on my phone?
Yes—there’s an official Tor Browser for Android. iOS users can use apps like Onion Browser.
Q2:Can Tor be hacked?
Tor itself is hard to hack, but attackers can target your device, use malicious exit nodes, or exploit careless user behavior.
Q3:Can I access Netflix or streaming services with Tor?
Not reliably. Many streaming platforms block Tor exit nodes. If streaming is your goal, a VPN is a much more stable and faster choice.
Q4:Do I need a VPN if I’m already using Tor?
Yes. Tor hides your IP through relays, but your ISP can still see you’re using Tor. A VPN adds another layer of privacy, preventing ISP monitoring and securing your connection outside Tor.
Q5:Will Tor slow down my internet?
Yes. Because your traffic passes through multiple relays worldwide, Tor is slower than regular browsing. A VPN usually offers faster speeds.