What email headers actually reveal
Every email carries a hidden “envelope” called the header. Beyond From/To/Subject, it lists servers that handled the message, timestamps, authentication results, and multiple Received: lines that outline the delivery path. When people set out to find IP address from email, they’re usually searching those Received lines for the earliest hop. That’s the theory.
In practice, modern platforms frequently inject their own IPs into those headers. If the sender used Gmail in a browser, for instance, header IPs typically point to Google, not the human sender’s home or mobile address. That’s by design; large email providers mask users’ network details to reduce doxxing and abuse.
Step-by-step: how to find the IP candidates in headers
Below is a simple, provider-agnostic workflow you can apply to most inboxes. (Menu names vary, but the concept is the same: reveal original headers, then search for Received.)
-
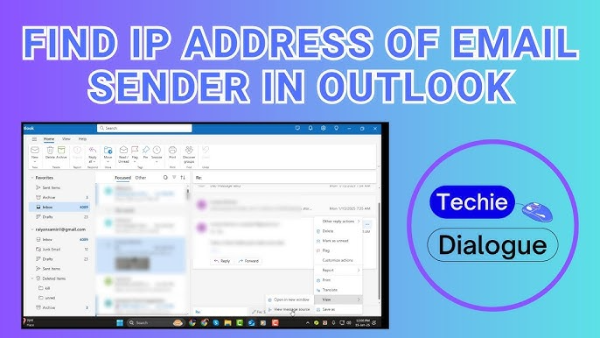
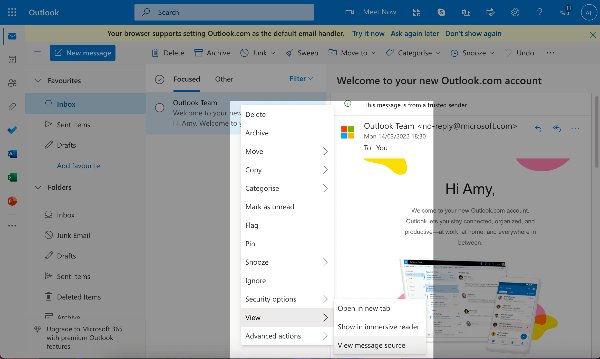
Open the full header/original message.
-
In Gmail, open the email → three dots ⋮ → Show original.
-
-
Search for “Received:” lines.
-
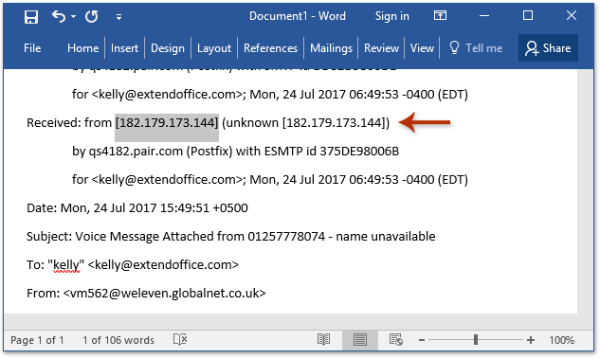
The oldest Received line (nearest the bottom of the header block) often shows the first server that accepted the message and an IP associated with that hop. Some people paste the full header into an analyzer to highlight IPs and hops.
-
-
Validate with a reputable analyzer (optional).
-
If header formatting confuses you, paste the entire header into a trusted tool to extract candidate IPs and geolocation info. (Tools referenced in the source article illustrate this process.)
-
-
Interpret cautiously.
-
A match doesn’t guarantee “the sender’s device.” For webmail and most big providers, the IP you find is commonly the service’s infrastructure—not the user’s residential IP. Use the next section’s rules of thumb to avoid false conclusions.
-
Why it’s usually not the sender’s IP

If a message originated from a browser session in Gmail (or most mainstream webmail), the header tends to expose a provider IP. The guide demonstrates that a header’s IP resolved to Google—confirming the address was Google’s, not the individual sender’s. That’s typical across major browser-based email services. So while it’s easy to pull an IP from the header, it’s often the email service’s IP, not the person’s.
Key takeaways
-
Webmail hides end-user IPs behind relays.
-
Desktop SMTP clients and self-hosted mail can behave differently, but many modern setups still obscure the endpoint.
-
Treat header IPs as “routing artifacts,” not proof of where a person lives or works.
Why someone might want your IP
Curious senders and malicious actors alike chase IPs for different reasons. With an IP, a party might tailor spam, restrict access (e.g., game server bans), attempt DDoS harassment, stalk, or try to resell data on shady forums. While this sounds scary, remember that mainstream email flows rarely leak your personal IP, and the probability of someone deriving your real-world location via an email you sent through webmail is low. Still, your email provider and ISP do know your IP and might disclose it if compelled under applicable laws and policies.
Legitimate use cases—and ethical boundaries
There are valid reasons to inspect headers:
-
Phishing triage: SOC analysts verify whether a message truly originated from a domain or known relay.
-
Abuse reporting: IPs in headers help identify a compromised host or open relay to report to admins.
-
Deliverability debugging: Mail admins trace hops to see where messages are delayed or rejected.
Even then, approach responsibly:
-
Don’t doxx. Avoid publishing supposed “origin IPs” of private individuals.
-
Avoid overreach. A provider IP does not equate to a sender’s apartment address.
-
Follow policy and law. If you’re part of an organization, use authorized tooling and escalation paths.
Protecting your own privacy: simple, modern defenses
If you care about preventing others from inferring where you are or building a behavioral dossier from your messages, combine the following measures.
1) Make sure your email service hides your IP
Most mainstream services already withhold end-user IPs in headers; confirm your provider’s behavior in its privacy docs or by inspecting a message you send to yourself.
2) Use strong authentication on your mailbox
Unique, long passwords plus 2FA keep attackers out of your inbox (and your headers). Password managers help generate and store strong credentials safely.
3) Block trackers in email
Disable automatic image loading, and consider tracker-blocking extensions to stop invisible pixels from reporting when/where you opened a message.
4) Hide your network address with free proxy VPN in UFO VPN
A VPN doesn’t change what your email provider shows in headers (those are provider IPs anyway), but it does harden the path between your device and the first hop:
-
Encryption on untrusted networks: Airports, hotels, and cafés can’t passively observe or tamper with your session.
-
IP masking: Sites you visit (and third-party trackers embedded in emails you open) see the VPN egress IP instead of your local one—useful when you want to hide IP address details from opportunistic profiling.
-
Smart Connect & Kill Switch: With UFO VPN, Smart Connect automatically picks a low-latency server for snappy inbox usage; a kill switch prevents accidental leaks if the tunnel drops.
💙4 Steps to open UFO VPN:


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







Pair a privacy-respecting email service with UFO VPN and basic hygiene (2FA, tracker blocking) for layered protection—especially when traveling or working remotely.
Quick reference: header-reading checklist
| Goal | What to do | What to expect |
|---|---|---|
| Validate routing | Open original headers and scan Received lines | Multiple server hops, timestamps |
| Extract an IP | Copy the earliest Received entry or use a header analyzer | Usually a provider IP for webmail |
| Geolocate | Look up the IP in a reputable database | Likely shows the mail provider’s data center |
| Decide action | Abuse report to hosting/email provider if needed | Provide full headers, not just an IP |
| Protect yourself | Use webmail that masks IP + UFO VPN, block images, 2FA | Less metadata exposure & safer sessions |
Responsible alternatives when you need real attribution
If you genuinely need to identify a harmful actor:
-
Preserve evidence: Keep the email intact with full headers.
-
Use platform channels: Report via the provider’s abuse address (e.g., abuse@provider).
-
Involve the right teams: If it’s criminal or involves sensitive targets, escalate to legal or law enforcement rather than running your own deanonymization.
Remember: attribution is hard and often unnecessary for day-to-day inbox safety.
FAQs
Can I really find an IP address from email headers?
Yes—headers contain Received lines with IPs of servers that handled the message. But with major webmail, that IP usually belongs to the email provider, not the human sender.
Why would someone want my IP address?
Motivations range from nuisance (targeted spam, bans) to abuse (stalking, DDoS). The chance of exposing your personal IP via normal webmail is low, but caution is smart.
Can my ISP or email provider reveal my IP?
They possess that data and may disclose it if compelled under relevant laws and policies. That’s one reason to value providers with strong privacy practices.
What’s the safest way to inspect headers?
Use your mail app’s “original”/“view source” option, copy the header into a reputable analyzer if needed, and avoid sharing headers publicly (they can contain identifiers). The UFO VPN walkthrough shows a lightweight, user-friendly approach.









