Types of Personal Information
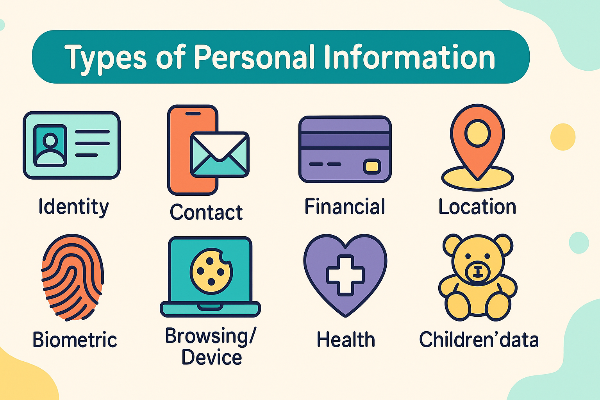
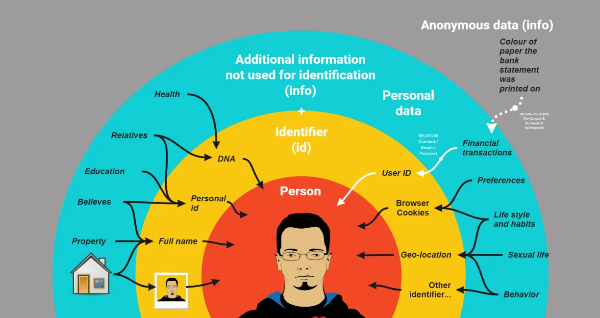
It’s easier to protect personal information when you recognize the categories and their risk levels. Use this quick mental model:
1) Basic profile data
Name, email, age range, city. Useful for account creation and notifications. Risk: phishing/spam if leaked.
2) Contact & identifiers
Phone, home address, IP/device IDs. Risk: SIM swap, account takeover, doxxing, persistent tracking.
3) Financial & transactional
Payment details, purchase history, subscription records. Risk: fraud, chargebacks, social-engineering.
4) Behavioral & interest graphs
What you click, read, watch, and the ads you interact with. Risk: profiling, targeted scams, discrimination.
5) Sensitive personal information
Health data, biometrics, precise location, sexual orientation, religious or political views. Risk: serious harm if exposed; many laws add extra protection.
How Personal Information Is Collected and Used

To protect personal information, it helps to see the pipeline:
You & your devices → apps, browsers, and operating systems collect usage and diagnostic data.
Networks & ISPs → your traffic reveals IP, DNS lookups, and timing metadata.
Websites & ad tech → cookies, pixels, and device fingerprints build cross-site profiles.
Platforms & data brokers → aggregate signals from many sources into dossiers sold for ads, credit/risk scoring, or resale.
Employers & schools → may add monitoring and device management on organization-owned hardware.
Legitimate uses (support, security, personalization) coexist with aggressive tracking. The result: your personal information can propagate beyond the services you intended to use.
Where Personal Information Leaks

Breaches make headlines, but everyday leaks are quieter:
-
Phishing pages capturing credentials
-
Weak or reused passwords enabling credential-stuffing across multiple accounts
-
Public Wi-Fi exposing traffic metadata or captive-portal manipulation
-
Malicious browser extensions reading pages and selling data
-
Third-party app permissions (contacts, photos, precise location) far beyond necessity
-
Oversharing in public profiles or cloud-shared links
-
Lost/unencrypted devices with auto-login turned on
Warning signs: unfamiliar login alerts, password reset emails you didn’t request, sudden card charges, strange devices in account security pages, or ads eerily tied to private activity.
How to Protect Personal Information
You don’t need to lock down everything at once. Run this playbook in order; each step measurably reduces the exposure of personal information.
1) Lock accounts with strong authentication
-
Use a password manager to create unique, long passwords.
-
Turn on multi-factor authentication (prefer app-based or security keys over SMS).
-
Regularly review “logged-in devices” and revoke anything you don’t recognize.
2) Minimize data at the source
-
When an app asks for access (contacts, photos, microphone, precise location), choose “While Using” or “Selected Photos.”
-
Audit permissions quarterly: remove anything non-essential, especially for background location.
-
In browsers, disable third-party cookies, review site permissions, and use privacy-respecting search.
3) Segment identities and devices
-
Create separate email aliases (shopping, finance, social) to reduce cross-linking of personal information.
-
Use browser profiles/containers for work vs. personal to compartmentalize cookies and logins.
-
Consider a dedicated device profile for kids or guests.
4) Secure the network path (especially on public Wi-Fi)
Private browsing removes local traces but does not encrypt traffic across the network. On airports, hotels, cafés, or campus Wi-Fi, use a reputable VPN:
-
UFO VPN encrypts your connection end-to-end on local networks, masking your IP from venue operators and reducing the chance of traffic inspection or manipulation.
-
✨Routine✨:


UFO VPN is an all-in-one VPN that offers unlimited access to 4K streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







-
A VPN doesn’t make you anonymous to sites you log into, but it shields the route where personal information is most exposed.
5) Reduce your public footprint
-
Set social profiles to private where appropriate; prune old posts and shared albums.
-
Remove public calendar links, drive shares, and map lists you no longer need.
-
Opt out of major data brokers where possible; many offer self-service portals.
6) Update and harden devices
-
Turn on automatic updates for OS, apps, browsers, and firmware (routers too).
-
Enable full-disk encryption on laptops and phones; use a strong device passcode.
-
Uninstall apps you don’t use—fewer apps mean fewer ways personal information can leak.
7) Prepare for “when,” not “if”
-
Enable alerts from your bank/credit card for new charges.
-
Store recovery codes for 2FA in an offline secure place.
-
Back up critical documents and photos securely so you can rebuild after a device loss or ransomware incident.
Run this checklist once, then revisit quarterly. It’s the fastest, lowest-stress way to protect personal information over time.
Personal Information Law You Should Know

Privacy regulations don’t replace your own defenses, but they give you rights over personal information:
-
GDPR (EU/EEA): rights to access, correct, delete, restrict processing, and data portability; requires lawful bases and transparency.
-
CCPA/CPRA (California) and similar state laws: rights to know, delete, and opt out of sale/sharing; heightened duties around sensitive personal information.
-
Sector-specific rules (HIPAA for health, COPPA for children) add protections for certain data types.
Practical takeaways:
-
Look for “Privacy” or “Do Not Sell or Share” options in account settings.
-
Use download-your-data tools to see what a service stores about you.
-
If a company mishandles personal information, you can lodge a complaint with regulators—sometimes this speeds resolution.
Data-Smart Habits for Everyday Life
To make protection stick, embed these micro-habits into your routine:
-
Pause before you post: Will future-you be comfortable if this appears in search?
-
Verify requests: Call the company back via the number on its website; never via a link in an unexpected message.
-
One minute for Wi-Fi: If you must use public Wi-Fi, connect UFO VPN before opening mail or banking.
-
Quarterly privacy tune-up: Calendar a 30-minute review of permissions, social visibility, and password health.
-
Minimal-share mindset: If a form asks for data that seems unnecessary, try leaving it blank or use an alias.
FAQs
What is personal information in plain terms?
Anything that identifies you or can reasonably be linked to you—names, emails, device IDs, IP address, purchase history, and sensitive data like health or precise location.
What’s the difference between personal information and sensitive personal information?
Sensitive personal information includes high-risk items—health data, biometrics, precise location, financial records, and children’s data—that deserve extra protection.
How often should I review permissions and privacy settings?
Quarterly is a good cadence. It keeps app creep in check and helps you notice new settings that can further protect personal information.
How do I protect personal information on social media?
Set profiles to private where possible, review audience defaults before posting, prune old content, and disable contact syncing. Use separate emails for sign-ups.
I got a breach notice—what now?
Change the password (and anywhere else it was reused), enable 2FA, review recent logins, and watch financial statements. Consider credit monitoring if payment data leaked.