What WEP, WPA, WPA2, and WPA3 Actually Mean

When people search WEP vs WPA vs WPA2 vs WPA3, they want simple definitions first:
-
WEP (Wired Equivalent Privacy) – The first Wi-Fi security method. Uses RC4 with weak key handling. Broken and deprecated.
-
WPA (Wi-Fi Protected Access) – A stopgap after WEP’s failure. Introduced TKIP (Temporal Key Integrity Protocol). Legacy and weak by modern standards.
-
WPA2 – Standardized AES-CCMP encryption. Still very common. Vulnerable if misconfigured (e.g., TKIP fallback) or with weak passwords.
-
WPA3 – The latest standard. Replaces pre-shared key handshakes with SAE (Simultaneous Authentication of Equals) for stronger resistance to offline guessing, adds individualized data encryption on open networks (OWE in related profiles), and improved protections for public Wi-Fi.
As a rule of thumb in WEP vs WPA vs WPA2 vs WPA3: choose WPA3-Personal where available, WPA2-Personal (AES-only) if older devices require it, and avoid WPA/TKIP and WEP entirely.
How Wi-Fi Encryption Works
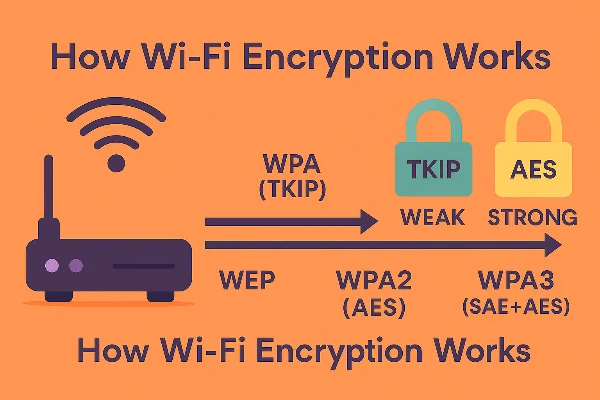
A big part of WEP vs WPA vs WPA2 vs WPA3 is understanding the ciphers and handshakes behind each name:
-
RC4 (WEP): A stream cipher with key-reuse and IV flaws. Attackers crack WEP in minutes.
-
TKIP (WPA): Bolted onto old hardware; patches some WEP issues but remains weak. Often caps throughput and is deprecated.
-
AES-CCMP (WPA2): Modern block cipher mode that authenticates and encrypts frames securely when paired with strong passphrases.
-
SAE + AES-GCM/CCMP (WPA3): SAE (also called Dragonfly) replaces the old PSK handshake, adding forward secrecy and better resilience against offline dictionary attacks. Data is protected with AES in robust modes (CCMP/GCM), and enhanced protections exist for open networks under WPA3-aligned profiles.
Takeaway: In the match-up WEP vs WPA vs WPA2 vs WPA3, the real leap is WPA3’s SAE and WPA2’s AES-CCMP. Avoid TKIP/RC4; select AES-only.
Wi-Fi Secure Setup: Home & Small Office
Here’s a clean process that aligns with the logic of WEP vs WPA vs WPA2 vs WPA3 while keeping onboarding simple:
-
Pick the right mode
-
Use WPA3-Personal if all clients support it.
-
If not, choose WPA2-Personal (AES-only) or WPA2/WPA3 Transitional briefly during upgrades. Disable TKIP.
-
-
Create a strong passphrase
-
14+ characters, mixed words/characters; avoid dictionary phrases.
-
-
Update firmware
-
Router/AP firmware and client drivers often include security fixes and WPA3 improvements.
-
-
Split SSIDs if needed
-
Put older IoT gear on a separate WPA2-AES SSID/VLAN; keep your main SSID on WPA3.
-
-
Disable WPS & legacy options
-
WPS pins and mixed TKIP modes weaken otherwise strong setups.
-
-
Use modern DNS & isolation
-
Enable client isolation for guest SSIDs and use secure DNS options on the router (DoT/DoH where supported).
-
-
Back up configs
-
Export your router config after locking in WPA3 and VLAN/guest settings.
-
These steps ensure your WEP vs WPA vs WPA2 vs WPA3 migration lands on a clean, modern baseline.
Public Wi-Fi Reality Check

Even the best choice in WEP vs WPA vs WPA2 vs WPA3 can’t fix café or airport Wi-Fi risks. Networks you don’t control may be misconfigured, have weak isolation, or run captive portals that intercept traffic before encryption is stable. That’s where a VPN adds a separate, end-to-end shield.
How free proxy VPN in UFO VPN fits
-
A VPN encrypts all your traffic between your device and the VPN server, hiding DNS and web destinations from hotspot operators and snoops.
-
It’s independent of WEP vs WPA vs WPA2 vs WPA3 on the local Wi-Fi. Even on secure WPA3 hotspots, a VPN keeps your browsing private from the venue.
Quick start with UFO VPN


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







A VPN doesn’t replace good Wi-Fi encryption, but in the daily WEP vs WPA vs WPA2 vs WPA3 conversation, it’s how you stay private on networks you can’t harden yourself.
Upgrade & Troubleshoot: From Legacy to WPA3

If your network is stuck on WEP/WPA—or even WPA2 with TKIP—use this structured upgrade path:
-
Inventory clients
-
List laptops, phones, printers, cameras, TVs. Note which ones support WPA3 or at least WPA2-AES.
-
-
Stage the transition
-
Create a temporary WPA2/WPA3 Transitional SSID for a week or two while you update devices.
-
Migrate critical clients first (workstations, laptops, phones), then IoT.
-
-
Harden after migration
-
Turn off transitional modes and TKIP; enforce WPA3-Personal (or WPA2-AES until everything is ready).
-
-
Fix common issues
-
Can’t connect after change: Forget the network on the client, re-join, and ensure AES-only.
-
Slow speeds: Mixed TKIP/AES or legacy rates enabled. Set AES-only and disable 802.11b rates.
-
Smart devices stuck on WPA2: Park them on an isolated WPA2-AES SSID or upgrade the hardware.
-
-
Monitor & maintain
-
Update router/AP firmware quarterly. Review connected-device lists and remove unknown MACs.
-
Keep your end goal front and center in WEP vs WPA vs WPA2 vs WPA3: WPA3-Personal on your primary SSID, with legacy devices isolated.
Practical Security Habits Beyond the Router

No matter how you resolve WEP vs WPA vs WPA2 vs WPA3, daily habits close the biggest gaps:
-
Use strong, unique passphrases for Wi-Fi and admin accounts; password managers help.
-
Lock down the router admin page with HTTPS and non-default credentials; disable remote admin unless required.
-
Segment guests/IoT onto a separate SSID/VLAN with client isolation.
-
Keep OS and browsers patched, and prefer HTTPS-only modes.
-
Turn on 2FA for email and critical accounts; email compromises often lead to network resets.
-
Use UFO VPN on any network you don’t fully trust—hotels, cafés, airports, co-working spaces.
These habits work hand-in-hand with the tech choices you make in WEP vs WPA vs WPA2 vs WPA3.
FAQs
Which should I use today in WEP vs WPA vs WPA2 vs WPA3?
Use WPA3-Personal. If some devices can’t join, fall back to WPA2-Personal (AES-only) while you phase out legacy gear.
Is WPA2 still safe?
Yes—WPA2-AES remains robust with strong passphrases, but WPA3 improves resistance to offline guessing and adds better protections for open/public scenarios.
Can I enable WPA/TKIP for compatibility?
Avoid TKIP. It weakens security and may throttle speeds. Keep your SSID on AES-only modes.
Why is WEP still an option on some routers?
Legacy support. Do not use it. WEP is trivially crackable.
Does a VPN replace Wi-Fi encryption in WEP vs WPA vs WPA2 vs WPA3?
No—router security controls the local link. A VPN (e.g., UFO VPN) encrypts traffic over the wider internet and hides your destinations from hotspot operators and ISPs.