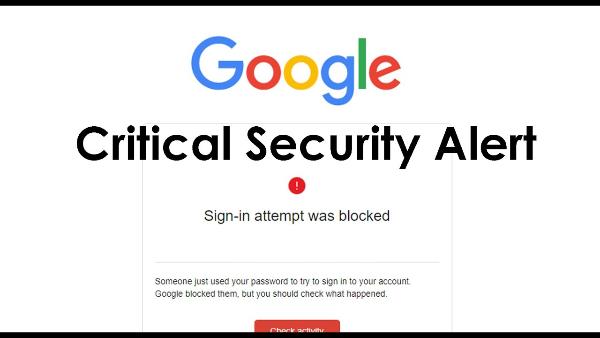
Recognize a hacked Google account

Before you begin the fix, confirm the red flags common in compromised Google/Gmail accounts:
-
Password no longer works or recovery prompts appear unexpectedly
-
“New sign-in” alerts you don’t recognize
-
Security settings or recovery email/phone changed
-
New filters/forwarding rules secretly redirect mail
-
Unfamiliar purchases or subscriptions in Google services (Google Pay, Google Play, YouTube Premium, Google Ads)
Financial red flags—like charges or ad spend you didn’t authorize—mean the attacker may be monetizing your account. Prioritize recovery, then audit bills and subscriptions.
Step-by-step: how to recover a hacked Google account

1) Try to sign in normally
Head to the Google sign-in page. If you still have access, immediately change your password and rotate recovery email, recovery phone, and 2FA settings. This shrinks the attacker’s window to act.
2) Use Google Account Recovery (if locked out)
If your password was changed, go straight to Google Account Recovery and follow the prompts. You’ll improve your chances by using a familiar device, browser, and location that you’ve signed in from before—Google’s systems recognize known patterns when verifying you.
3) Verify identity thoroughly
Provide old passwords, recovery codes, and answers as precisely as you can. If you have backup codes from 2FA, use them. If you’re asked to wait and try again later, do it; repeated failed attempts can reduce success rates.
4) Regain access, then change core credentials
Once inside, immediately:
-
Set a new password (long, random, stored in a password manager)
-
Update recovery email and phone
-
Re-enroll 2FA (authenticator app preferred) and generate fresh backup codes
Clean and secure the account after recovery

Attackers often leave behind persistence mechanisms. Systematically check:
A) Sessions & devices
-
Visit your Google Security page → Your devices → Sign out of anything unfamiliar.
-
Review Recent security activity and address any unrecognized sign-ins.
B) Gmail settings
-
Filters & Blocked Addresses: Delete suspicious filters that auto-forward, delete, or label mail.
-
Forwarding & POP/IMAP: Disable any forwarding you didn’t set up; reset app-specific passwords if used.
-
Send mail as: Remove unknown “send as” addresses. (Criminals sometimes add aliases to impersonate you.)
C) Third-party access
-
In Security → Third-party apps with account access, remove any app you don’t recognize or no longer need. Revoke OAuth tokens used by old tools or plug-ins.
D) Password resets elsewhere
-
Use your fresh password manager to rotate banking, shopping, social, and cloud passwords that use your Gmail for login/resets. Prioritize high-risk accounts (finance, crypto, cloud storage).
These “deep clean” steps mirror the essential hygiene recommended in reputable recovery guides and the walkthrough.
Protect payments, purchases, and ads

A compromised Google account can lead to Google Pay/Play fraud or Google Ads misuse:
-
Open Payments & subscriptions and Order history to spot unauthorized charges or ad spend.
-
Cancel unfamiliar subscriptions, dispute charges, and contact support where needed.
-
Audit Google Ads (if you use it) for rogue campaigns or billing changes.
Financial misuse is specifically called out in practical recovery advice; address it the same day you regain control.
Privacy and reliability while you recover: where VPN helps
A VPN doesn’t replace Google’s recovery steps, but it protects the path you use to do them—especially on hotel, café, airport, or campus Wi-Fi:
-
Encrypt connections on untrusted networks: Thwarts hotspot owners or snoops from monitoring your logins and recovery traffic.
-
Mask your IP from opportunistic tracking: Sites and embedded pixels see your VPN exit IP, not your local address.
-
Stabilize your connection while traveling: If regional quirks disrupt access, a nearby free proxy VPN in UFO VPN server can provide a cleaner route to Google services (always follow local laws and platform terms).
Useful features while recovering: Smart Connect (fastest nearby server), Split Tunneling (route only your browser/recovery tab through VPN), and a Kill Switch (prevents traffic leaks if the tunnel drops). Use UFO VPN as your privacy baseline whenever you must log in from shared networks.
🩵4 Steps to Turn UFO VPN on:


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







Prevent the next takeover: build modern defenses

1) Upgrade to strong 2FA or passkeys
Use an authenticator app or hardware security key (YubiKey, Titan) rather than SMS. Where available, enable passkeys for phishing-resistant sign-ins. Rotate new backup codes and store them offline.
2) Password manager + unique passwords
A breached password reused across services is the #1 shortcut for attackers. Let a manager generate and store 16- to 20-character random passwords for every site.
3) Security Checkup
Run Google’s Security Checkup to review devices, third-party access, weak passwords, and recent events in one dashboard.
4) Phishing and malware basics
-
Don’t approve unexpected 2FA prompts (“MFA fatigue”).
-
Disable auto-loading of remote images in email to reduce tracker leakage.
-
Scan devices for malware (keyloggers steal passwords before 2FA even matters).
Leading consumer security outlets reinforce these fundamentals for post-hack hygiene.
Quick reference checklist
-
Try normal sign-in; if in, change password + recovery info immediately.
-
If locked out, use Google Account Recovery—prefer a known device/browser/location.
-
After entry, rotate password, set strong 2FA/passkeys, generate new backup codes.
-
Terminate unknown sessions; remove suspicious filters, forwarding, and third-party access.
-
Audit payments/subscriptions and dispute unauthorized charges.
-
Run Security Checkup; rotate passwords elsewhere; scan for malware.
-
Use UFO VPN on public Wi-Fi while working through recovery.
FAQs
How do I recover a hacked Google account if my password was changed?
Use Google Account Recovery and follow the prompts. Your odds improve if you attempt recovery from a familiar device/browser/location you’ve previously used to sign in.
What should I do first once I get back in?
Immediately change your password, rotate your recovery email/phone, re-enroll 2FA (authenticator or security key), and generate new backup codes. Then sign out of unknown devices.
How do I find hidden changes an attacker made to Gmail?
Check Filters & Blocked Addresses, Forwarding & POP/IMAP, and Send mail as for rules or aliases you didn’t add. Remove suspicious third-party app access under Security.
What about unfamiliar charges in Google Pay/Play or Google Ads?
Review Payments & subscriptions and your Order history/Ads billing. Cancel rogue subscriptions, dispute charges, and contact support if needed—financial misuse is a known post-hack risk.