What Is Software Piracy?

At its core, software piracy is using software in ways the license doesn’t allow. Licenses may limit the number of devices, the geography, the features, or whether the software is for personal or commercial use. When those terms are bypassed—by cracks, key generators, shared accounts, or casual “I installed it everywhere”—that’s software piracy.
Why it matters:
-
Security: Cracked installers commonly bundle trojans or credential-stealers.
-
Privacy: “Free” pirated builds often exfiltrate telemetry or add adware.
-
Reliability: No authentic updates, patches, or support—bugs and vulnerabilities pile up.
-
Legal & financial: Civil claims, statutory damages, and in some regions criminal penalties.
-
Ethics: Developers, including small studios, depend on license revenue to ship fixes and features.
Types of Software Piracy
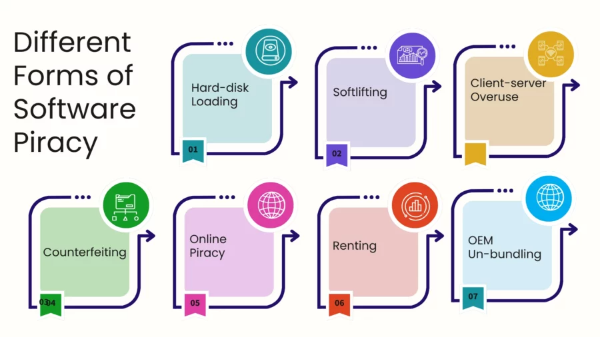
Understanding the types of software piracy helps you spot risk before it bites.
-
Counterfeiting
Selling or downloading modified copies that pretend to be legitimate. Often found on shady marketplaces or “too-good-to-be-true” bundles. -
Cracks & keygens
Bypassing activation with patched binaries or key generators. Popular on warez forums—also a popular way to install malware. -
Softlifting
Buying one consumer license and installing it on multiple personal or workplace devices in violation of the EULA. -
Client-server overuse
Exceeding concurrent seat limits on network licenses; common in labs or studios that “temporarily” over-provision. -
Hard-disk loading / gray resellers
Devices sold with preinstalled unlicensed software. The buyer inherits legal and security problems on day one. -
Account & key sharing
Sharing a personal subscription or enterprise key with friends or contractors—seems harmless, but violates most licensing terms and nullifies support.
Each pathway may look “free,” but every one raises your odds of compromise and liability.
Software Piracy Laws and Real-World Risks

Software piracy laws vary by country, but most jurisdictions recognize copyright infringement, license breach, and trafficking in circumvention tools as actionable.
What risk looks like:
-
Civil penalties: Fines, damages, and in enterprise settings, costly settlements after audits.
-
Criminal exposure: In some regions for large-scale distribution or commercial exploitation.
-
Employment/contract risks: Compliance clauses can void deals or trigger termination.
-
Security incidents: Pirated packages are a leading source of ransomware and data theft.
-
Operational downtime: No vendor support means longer outages and slower incident response.
Bottom line: the “savings” of software piracy evaporate quickly when you price security incidents, downtime, and potential legal exposure.
Anti-Piracy Measures You Can Use Today

Whether you’re an individual or a team, these anti-piracy measures reduce risk and keep you compliant—without slowing you down.
For individuals
-
Buy from official stores only. App Store, Google Play, vendor sites, or recognized resellers.
-
Verify the publisher. Check developer name, domain, and code-signing. Avoid “repacked” builds.
-
Keep updates on. Security patches close the bugs pirates exploit.
-
Use a password manager & 2FA. If a pirated installer steals a password, 2FA blocks account takeover.
-
Scan downloads. Reputable endpoint protection can flag tampered binaries.
-
Delete cracked tools. If you used one in the past, assume exposure—change credentials and reinstall clean.
For teams & businesses
-
Centralize purchasing. One owner for licenses; no side deals or “free” installs.
-
Maintain a software bill of materials (SBOM). Know what’s installed, where, and who owns it.
-
Automate patching. Endpoint management (MDM/UEM) for OS and apps; staggered rings for testing.
-
Document entitlements. Save invoices, license keys, and seat assignments for audit-readiness.
-
Least-privilege installs. Standard users can’t add software; admin elevation is time-boxed and logged.
-
Offboarding checklist. Reclaim seats and revoke access when people leave.
These moves don’t just deter software piracy—they reduce attack surface and make support easier.
Legal, Safer Alternatives to Software Piracy

Avoid software piracy by picking one of these legitimate paths:
-
Freemium & community editions: Many dev tools and creative apps offer powerful free tiers.
-
Open-source software: Mature projects (with active maintainers) rival paid tools for many tasks.
-
Educational & non-profit discounts: Students, teachers, and NGOs often qualify for deep cuts—or free access.
-
Short-term subscriptions: Pay for the month you need, then cancel.
-
Web apps / SaaS: Browser-based tools reduce install risk and keep you on current builds automatically.
-
Vendor trials & refunds: Test legally; if it’s not a fit, move on—no cracks required.
Choosing any of these lets you skip the legal and security baggage of software piracy while meeting your budget.
Online Privacy & Security Notes
A VPN can strengthen your anti-piracy measures by protecting the network path—but it doesn’t legalize infringement. Use free proxy VPN in UFO VPN for legitimate privacy and security:
-
Public Wi-Fi safety: Airports, hotels, and cafés can log or inject traffic. A VPN encrypts DNS and web requests end-to-end on local networks.
-
Account protection: Mask your IP from opportunistic profiling and reduce session hijacking on hostile networks.
-
Update integrity: Encrypted tunnels help ensure patches and installers aren’t tampered with by on-path actors.
A practical routine with UFO VPN (legitimate use only):


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







Build a No-Piracy Toolkit (Personal & Team)
Make the safe path your default so software piracy never looks tempting:
-
Curated app list: Maintain a short “approved alternatives” list (paid + open source) for common tasks.
-
Receipts & keys vault: Store proof of purchase and license data in a secure password manager.
-
Quarterly audit reminder: Calendar a lightweight review of installs vs. entitlements.
-
Security baselines: Hardware encryption on; browser isolation for downloads; email image blocking to neuter tracking pixels.
-
Developer mode discipline: If you sideload for testing, keep that profile separate and locked down.
Small, repeatable habits beat one-time cleanups.
FAQs
Is software piracy always illegal?
Yes—using software outside its license violates software piracy laws. Some regions add criminal penalties for large-scale distribution. Always choose licensed or open-source options.
What are the safest alternatives to pirated software?
Freemium/community editions, open-source tools, educational discounts, and short-term subscriptions—each avoids the legal and security risks of software piracy.
Can a VPN make pirated downloads safe or legal?
No. A VPN protects the network path and your privacy on untrusted Wi-Fi, but it does not legalize software piracy or clean malicious installers.
How can a small team stay compliant without big costs?
Centralize purchasing, track seats, adopt open-source where viable, and use short-term subscriptions. Automate patching and keep invoices/keys in a shared vault.
What are the biggest security risks of cracked apps?
Malware (stealers, RATs, ransomware), adware, and disabled updates. You also lose vendor support and patch pipelines.