What Is the Tor Browser?
The Tor Browser is a free, open-source software that allows users to browse the internet anonymously by routing their traffic through a network of volunteer-operated servers known as "relays." The primary purpose of the Tor Browser is to obscure the user's location and browsing activity, providing a higher level of privacy than standard web browsers.
Tor stands for The Onion Router, named after the multiple layers of encryption it uses to protect your identity. It is widely used by those who want to keep their internet activity private, access restricted content, or browse the dark web.
How Does the Tor Browser Work?
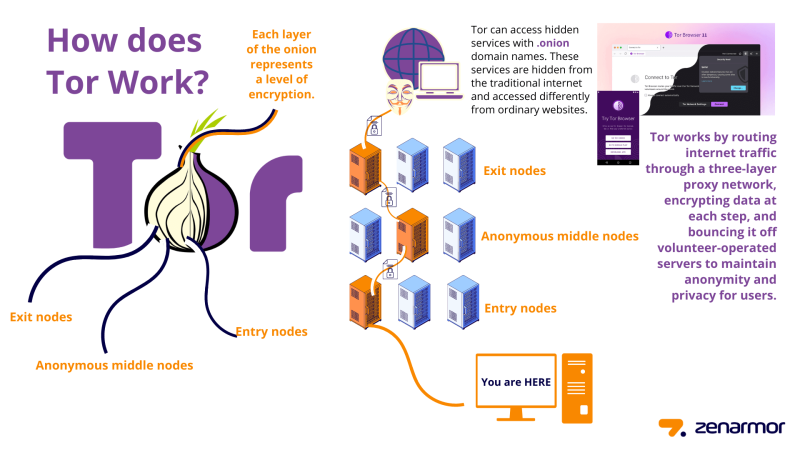
The Tor Browser operates by routing your internet traffic through a series of encrypted "nodes" or relays. Each relay only knows the location of the previous and next relay in the chain, making it extremely difficult for any one entity to trace your browsing activity back to you.
Key Features:
-
Multi-layered Encryption: Your data is encrypted multiple times, like peeling back the layers of an onion (hence the name). Each relay decrypts a layer, revealing the next destination until you reach your final destination.
-
Randomized Routes: Every time you use Tor, your traffic is routed through a different series of relays, making it harder to trace your location or activity.
-
Exit Nodes: After passing through the relays, your traffic exits the Tor network via an "exit node." This node sends your request to the website you're visiting. However, the website sees the exit node’s IP address, not yours.
Is the Tor Browser Safe?
While the Tor Browser offers a high level of privacy, it's important to understand that it isn't entirely risk-free. Here are the main factors that determine the safety of using Tor:
Pros of Tor Browser:
-
Strong Anonymity: The encryption and routing through multiple nodes make it very difficult to track your activity.
-
Bypass Censorship: Tor is commonly used in countries with heavy internet censorship, allowing users to access restricted websites.
-
Access to the Dark Web: Tor allows access to websites with ".onion" domains that aren’t indexed by traditional search engines.
Cons of Tor Browser:
-
Vulnerabilities in Exit Nodes: Since your traffic exits the Tor network through exit nodes, these nodes can potentially monitor your traffic if it is not encrypted at the application level (i.e., HTTP traffic instead of HTTPS).
-
Potential for Malware: Although the Tor network is designed to anonymize users, some websites may still expose you to malicious scripts or malware.
-
Reduced Speed: Due to the multiple layers of encryption and the routing through different nodes, Tor can significantly slow down your browsing experience.
-
Not Immune to Traffic Correlation Attacks: In certain circumstances, if a malicious entity controls both the entry and exit nodes, it could potentially correlate your traffic and determine your identity.
While Tor enhances your online anonymity, it doesn't protect you from all forms of surveillance or attack, especially if you fail to implement additional precautions such as using encrypted sites (HTTPS) or pairing it with a VPN like UFO VPN.
How to Stay Safe While Using Tor
To maximize the safety of using Tor, consider these additional precautions:
1. Use HTTPS Websites
Always prioritize websites that use HTTPS (indicated by the padlock icon in the address bar). HTTPS encrypts the data between your browser and the website, ensuring that even if someone intercepts your traffic at an exit node, they can't easily read your data.
2. Avoid Logging into Personal Accounts
Logging into your personal accounts (e.g., Gmail, Facebook) while using Tor can compromise your anonymity. Websites may correlate your real identity with your activity. If you must log in, consider using a pseudonymous account.
3. Keep Your Software Up-to-Date
Ensure that your Tor Browser and any related software are regularly updated to patch known vulnerabilities.
4. Use Best free VPN for Added Privacy
While Tor provides great anonymity, combining it with a VPN such as UFO VPN provides an additional layer of security. UFO VPN encrypts your traffic and hides your IP address, making it harder for anyone to trace your activity, even if they have control over some of the Tor network's exit nodes.
How to Delete Tor Browser
If you decide that Tor is no longer necessary or want to uninstall it for any reason, here’s how you can delete Tor Browser from your device:
For Windows:
-
Open the “Control Panel” and go to “Programs and Features.”
-
Find “Tor Browser” in the list, select it, and click Uninstall.
-
Follow the on-screen prompts to complete the uninstallation.
-
Optionally, you can also delete the Tor Browser folder from your “Program Files” directory.
For macOS:
-
Open the "Applications" folder.
-
Find “Tor Browser,” right-click on it, and select Move to Trash.
-
Empty the Trash to fully remove Tor from your system.
For Linux:
-
Use your terminal to run the following command:
-
You can also delete any remaining Tor Browser files by navigating to the folder where Tor was installed and removing it manually.
How to Download UFO VPN


UFO VPN is an all-in-one VPN that offers unlimited access to 4D streaming like Netlfix, Disney Plus, no-ping gaming as PUBG, Roblox, CODM and social networking for YouTube, X, Facebook and more.




Unlock Pro Features
If you have upgraded to premium plan , feel free to enjoy premium servers for 4K streaming and advanced features like Kill Switch, Split Tunneling, and gaming acceleration. Your Mac is now fully optimized and protected. Inaddition to basic functions, we recommend you turn on

Verify Your IP Now
Use UFO VPN's " What is My IP " feature to see your new IP and location. This confirms your connection is secure, anonymous, and ready for safe browsing online anywhere at any time.







Conclusion
The Tor Browser is a powerful tool for maintaining online anonymity and privacy, but it’s not without risks. Is the Tor Browser safe? While it offers significant protection against tracking and surveillance, there are potential vulnerabilities, especially related to exit nodes and malware. To maximize your security, use Tor in combination with best practices such as accessing HTTPS websites and avoiding logging into personal accounts.
For even stronger privacy, consider pairing Tor with UFO VPN, which encrypts your internet traffic and protects your real IP address. By doing so, you can fortify your defenses and enjoy a safer, more anonymous browsing experience.