What is an IP Address
An IP (Internet Protocol) address is a unique string of numbers assigned to your device by your Internet Service Provider (ISP). It acts like a digital mailing address, enabling your device to send and receive data over the internet. There are two types of IP addresses: dynamic IPs(which change periodically) and static IPs (which remain the same). While dynamic IPs are more common for personal use, static IPs are often used for businesses or specific applications like hosting websites.
Your IP address reveals certain information about you, such as your approximate geographical location (city, state, or zip code) and your ISP. While it doesn’t directly disclose personal details like your name or phone number, it can be a starting point for hackers to gather more sensitive information.
Is Tracing an IP Address Legal or Not
Tracing an IP address is generally legal, provided it is not used for criminal purposes. Websites, apps, and ISPs routinely collect IP addresses for legitimate reasons, such as improving services or preventing fraud. However, when individuals or organizations use this information maliciously, it becomes a legal and ethical issue.
Legal Uses
For example, employers may monitor employees’ online activity using their IP addresses, but this must be done within the bounds of the law. Similarly, law enforcement agencies may trace IP addresses as part of criminal investigations, but they require proper authorization to do so.
How Can Others Find Your IP Address
Cybercriminals can obtain your IP address through various methods, many of which are surprisingly simple. Here are some common ways your IP address can be exposed:
Clicking on Links or Ads
Every time you click on a link or an ad, your IP address is shared with the server hosting that content. Malicious ads or links can be designed to capture your IP address and other data.
Visiting Websites
Websites routinely collect IP addresses for analytics and security purposes. If a website is compromised, hackers can access this data.
Using Public Wi-Fi
Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your internet traffic and capture your IP address.
Participating in Online Forums or Social Media
When you post on forums or use social media, your IP address can be logged by the platform. In some cases, administrators or hackers can access this information.
Peer-to-Peer (P2P) File Sharing
P2P networks, often used for sharing files, expose your IP address to other users on the network. This makes it easy for hackers to target you.
Phishing and Social Engineering
Hackers may use deceptive tactics to trick you into revealing your IP address. For example, they might send you a fake email or message asking you to click on a link that captures your IP.
Connecting to Fake Wi-Fi Hotspots
Cybercriminals can set up fake Wi-Fi networks in public places. When you connect, they can capture your IP address and other sensitive data.
What Can Hackers Do with Your IP Address
Once a hacker has your IP address, they can use it for a variety of malicious purposes. Here are some of the most common threats:
Track Your Location
While your IP address doesn’t reveal your exact address, it can provide a general idea of your location, such as your city or zip code. Combined with other information, this can be used to pinpoint your whereabouts.
Steal Personal Information
Hackers can use your IP address as a starting point to gather more sensitive information about you. For example, they might use it to launch phishing attacks or trick service providers into revealing your personal data.
Launch Cyberattacks
With your IP address, hackers can attempt to hack into your device or network. They might exploit vulnerabilities in your router or use brute force attacks to gain access.
Distributed Denial of Service (DDoS) Attacks
A DDoS attack involves flooding your device or network with excessive traffic, causing it to crash or become unavailable. Hackers can use your IP address to target you with such attacks.
Sell Your Data on the Dark Web
Your IP address, combined with other personal information, can be sold on the dark web. This data can then be used for identity theft or other fraudulent activities.
Frame You for Illegal Activity
Hackers can use your IP address to conduct illegal activities, such as downloading pirated content or accessing restricted websites. This can make it appear as though you are responsible for these actions.
Monitor Your Online Activity
Employers, ISPs, or even hackers can use your IP address to track your online activity. This can lead to privacy violations or targeted advertising.
How to Protect Your IP Address
Given the risks associated with IP address exposure, it’s essential to take steps to protect yourself. Here are some effective strategies:
Use a VPN
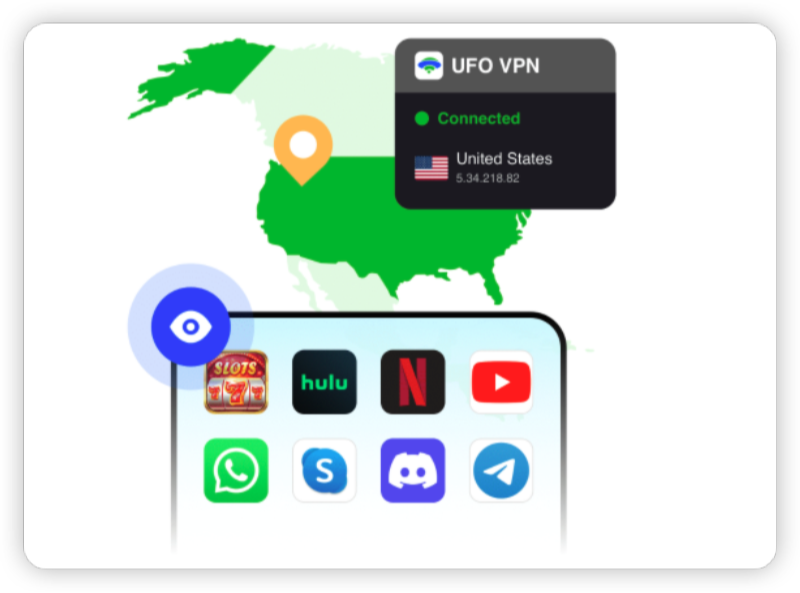
A Virtual Private Network (VPN) is one of the most effective tools for hiding your IP address. It routes your internet traffic through a secure server, masking your real IP address and encrypting your data. This makes it virtually impossible for hackers to track your online activity.
Choose a Reliable VPN
We recommend the trustworthy UFO VPN, with 3000+ servers in 50+ countries globally. The premium service on UFOVPN always ensures faster speeds and better privacy protection online.
Select a Suitable Server
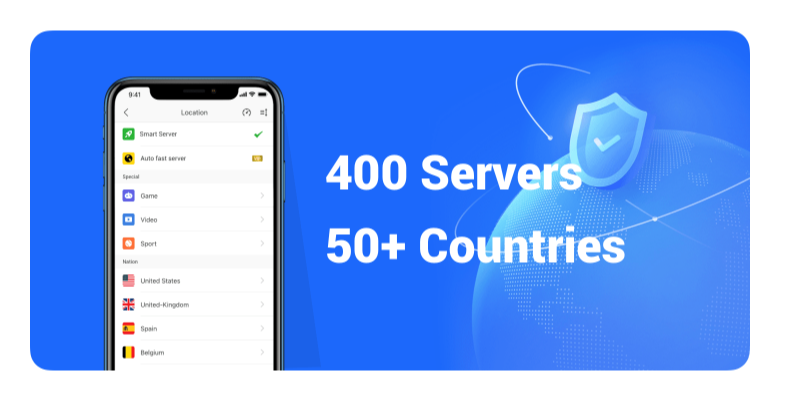
Connect to a Region Where the blocked service Is available in this country (e.g. the United States, UK, etc.).
Access the Blocked Platform via the Official Website
Log in to your account on the official website and start browsing now. Now you are free of worries like denied access, pop-up ads and malware anytime and anywhere!
Remember to enable the Kill Switch to protect your data in case of connection drops.
Enable a Firewall
A firewall acts as a barrier between your device and the internet, blocking unauthorized access. Ensure your firewall is enabled and properly configured to protect your network.
Update Your Router
Routers are a common target for hackers. Regularly update your router’s firmware and change the default password to a strong, unique one.
Avoid Public Wi-Fi
Public Wi-Fi networks are often unsecured, making them a prime target for hackers. If you must use public Wi-Fi, connect through a VPN to encrypt your data.
Be Cautious Online
Avoid clicking on suspicious links, ads, or emails. These can be used to capture your IP address or install malware on your device.
Use Antivirus Software
Antivirus software can detect and block malicious activity, including attempts to steal your IP address. Ensure your antivirus is up to date and running at all times.
Monitor Your Online Accounts
Regularly check your online accounts for unusual activity. If you notice anything suspicious, change your passwords immediately and enable two-factor authentication (2FA).
How a VPN Protects Your IP Address
A VPN is a powerful tool for safeguarding your IP address and enhancing your online privacy. Here’s how it works:
Hides Your IP Address
A VPN masks your real IP address by assigning you a new one from its server network. This makes it difficult for hackers to track your online activity.
Encrypts Your Data
A VPN encrypts your internet traffic, ensuring that even if hackers intercept it, they cannot read the data.
Bypasses Geo-Restrictions
A VPN allows you to access content that may be restricted in your region by routing your traffic through servers in other countries.
Prevents Tracking
By hiding your IP address, a VPN prevents advertisers, ISPs, and hackers from tracking your online behavior.
Additional Benefits of Using a VPN
Beyond protecting your IP address, a VPN offers several other advantages:
Enhanced Security
A VPN encrypts your internet traffic, protecting it from hackers, especially on unsecured networks like public Wi-Fi.
Privacy Protection
A VPN prevents ISPs, advertisers, and websites from tracking your online activity, giving you greater privacy.
Access to Restricted Content
A VPN allows you to bypass geo-restrictions and access content that may be blocked in your region.
Safe File Sharing
A VPN encrypts your data during file sharing, protecting it from interception.
Protection on Multiple Devices
Many VPNs, like UFOVPN, allow you to protect multiple devices with a single account, ensuring comprehensive security.
Conclusion
Your IP address is a critical part of your online identity, but it can also be a vulnerability if it falls into the wrong hands. By understanding the risks associated with IP address exposure and taking proactive steps to protect yourself, you can significantly reduce the likelihood of cyberattacks and maintain your online privacy. Using a VPN like UFOVPN is one of the most effective ways to safeguard your IP address and secure your internet activity. Stay vigilant, adopt best practices, and enjoy a safer, more private online experience.